A Malware's Tale or How I suspect Hackers are using Zoom Player as part of their malware campaign

A scary start
It began on a cold night in ~January.
A person posted on Zoom Player’s sub-reddit they initially thought Zoom Player was a virus, but looking into it they found it odd that there's an official forum that looks legit.
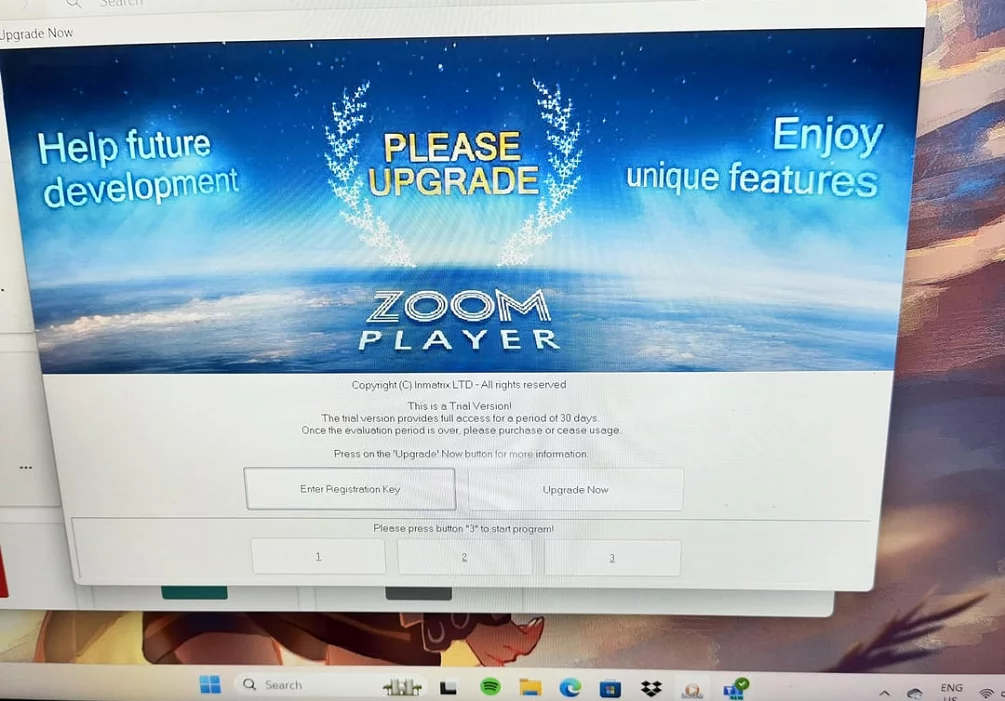
Said person explained that they did a clean Windows 11 install and found a copy of Zoom Player auto-running at boot, requesting to upgrade. "That was strange" I thought to myself, "How is that even possible?!".
Investigating
I tried digging in. I asked the person in private if they used a "Special Build" of Windows and the reply was interesting. They wrote that they used a "Special Program" to activate windows, a PowerShell script I never heard of.
I decided to dig deeper. I managed to find the Discord server the PowerShell script author was using and managed to chat with him and review the script. The author denied everything, his only interest was subverting Microsoft's activation, not spreading malware.
Unfortunately, even though the script’s author was swimming in the murky waters of the internet, I reviewed the script as best I could and didn’t find a connection to the malware infestation. Perhaps I missed it, but the chances were low, I was still missing something.
More reports start to come in
Then in the last few weeks, I received multiple reports, both on Zoom Player's sub-reddit and privately in chat. More people were reporting that Zoom Player's "upgrade" dialog was popping up on their screen, even though they never installed it.
Fortunately, one of the people reporting this issue finally agreed to share the actual infestation vector (most of the others disappeared as soon as I told them they should re-install Windows), a supposedly cracked version of "Driver Easy Pro" they found in a google search. I was able to obtain the link which led to a Brazilian Portuguese language website for pirated software.
Reviewing the malware
I downloaded a zip file which contained a password protected RAR file (along with a text file showing what the password is), a basic system to avoid Anti-Virus scans of downloaded files.
And this is when things became a bit strange.
The “Setup.exe” file had an internal description of "DualSafe Password Manager", not "Driver Easy Pro". The EXE was digitally signed by "Chengdu XiaoShanHu Information Technology Co.,Ltd." using "Sectigo RSA Time Stamping Signer #3" at "Monday, March 20, 2023 13:42:44".
It had what appeared to be copies of madExcept, a genuine commercial software development crash reporting tool. But again, it was digitally signed by "Chengdu XiaoShanHu Information Technology Co.,Ltd." on "Thursday, January 05, 2023 09:30:55" and not by the original author (a well known software developer that also happens to be the author of MadVR).
There were many more strange files, like "tika.png" which turned out to be BSCMAKE.EXE (digitally signed by Microsoft), "upd.dll" which turned out to be 360Installer.exe (digitally signed by "Beijing Qihu Technology Co., Ltd.") and "ripp.rf" which turned out to be "BackupToUrl.exe" (digitally signed by Microsoft).
And to make things even stranger, there was "zlib.dll" which in actually was "AdobeIPCBrokerCustomHook.exe" with a valid digital signature from "Adobe Inc." on "Friday, April 22, 2022 13:26:21".
A stealthy infection
None of these files came up as infected on VirusTotal. And I couldn't locate Player in there. I'm assuming this initial setup just creates an initial foot-hold installation which later downloads additional “modules” to extend functionality.
I submitted my findings to a malware security focused forum. One of the researchers did an initial investigation, reporting that there’s a strong possibility that the malware is in fact Lumma Stealer, a Russian based information stealing malware for rent that even has its source code to purchase in case you want to create your own variants.
The researcher said he suspects that the malware was exploiting a bug in the setup EXE for DualSafe Password Manager that can be abused to side-load DLL libraries containing the malware. Since the actual EXE is not infected, you will not get any Anti-virus warning messages when trying to run it or if you scan the files.
What you should do
If you suffered this infection, you are advised to reinstall windows and replace all your important passwords. It also helps to enable 2FA authentication where available, but even if you enabled 2FA previously, you are still required to change your passwords or at the very least logout of every browser session as “Stealer” malware can steal activate browsing sessions, allowing hackers to bypass passwords and 2FA authentications if you were previously logged into an account.
What Zoom Player has to do with it
As for why this is happening to Zoom Player? Zoom Player is a media player with a powerful and easy to use API (programming interface) that can be used remotely to show and control videos. I'm guessing the hackers included Zoom Player as part of their tool infrastructure “modules”. You can imagine how scary it would be to sit at your computer and all of a sudden a video pops up as part of a threatening ransomware campaign.
Luckily for the victims of this fiendish scheme, the hackers were too lazy to realize that after a certain period, Zoom Player shows an upgrade dialog, raising red flags and exposing their activities.
In conclusion
As I'm finalizing this post, more people contacted me in private, reporting they suffered the same issue when installing "a cracked plugin folder for FL studio" , an update to "the legend of zelda breath of the wild" or several other pirated apps and games. Each person reported downloading the pirated software from a different source, giving us a hint into how widespread this issue is.
Unfortunately for me, the hacking group’s actions paints Zoom Player in a bad light and there's nothing I can do about it other than sharing my tale.
I hope it was interesting.